A Pumpkin Guide to SAP Security in Your S/4 HANA Migration
As businesses increasingly turn to SAP S/4 HANA to streamline operations and drive digital transformation, the importance of robust security measures cannot be overstated. A successful migration or implementation of S/4 HANA demands a well thought out SAP security strategy and approach to safeguard critical data and processes and fully leverage the exciting new functionality and possibilities offered by S/4 HANA. Whether you're an executive overseeing the project or an SAP security professional navigating the technical intricacies, here's our guide to help you navigate the complexities of SAP security in your S/4 HANA project.
Early Planning and Assessment
An effective S/4 HANA migration or implementation needs thorough planning. Here's a detailed breakdown of the key steps involved in this critical phase.
1. Conducting a Comprehensive Security Assessment:
Start by being clear on potential vulnerabilities, weaknesses and compliance gaps in your existing environment that will need to be addressed.
Evaluate the effectiveness of existing security controls, to identify areas for improvement and determine what you can roll forward to your new system.
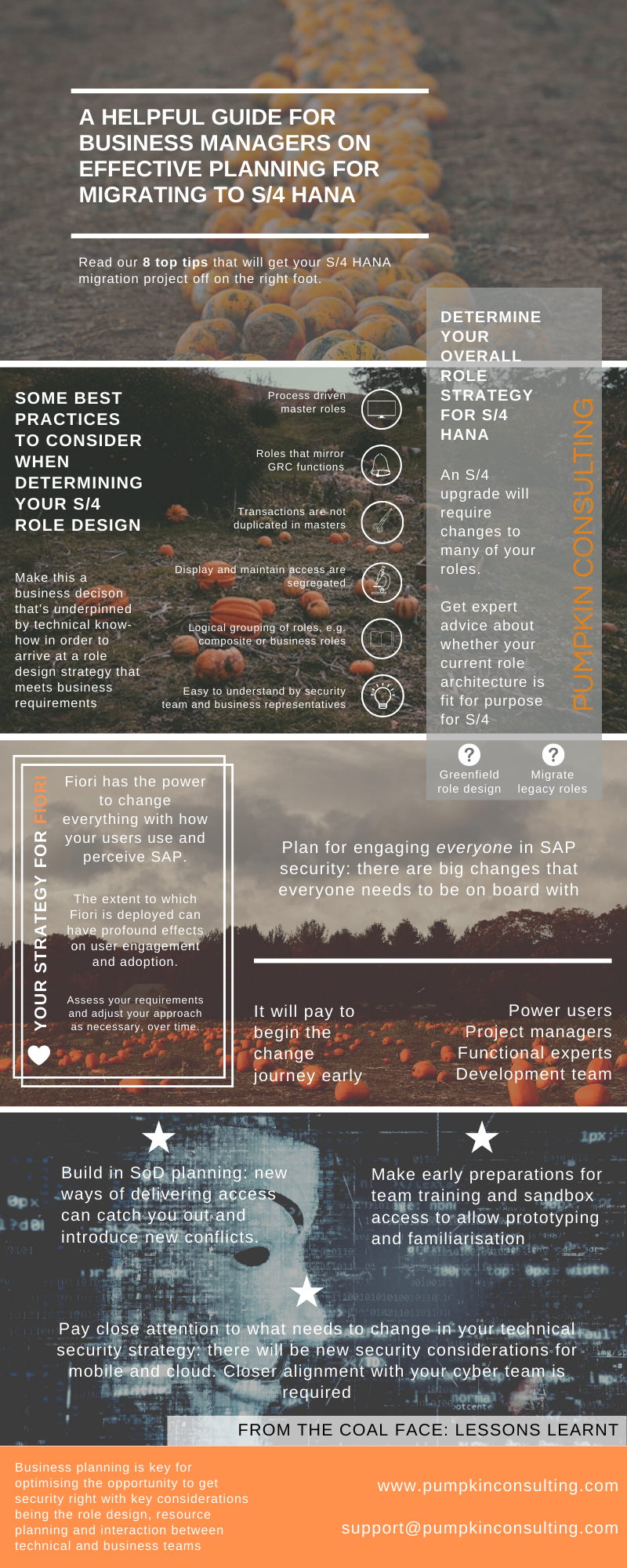
At a detailed level, your team should be looking at this stage about whether your role design is fit for purpose and whether a new access strategy is needed for S/4.
2. Establishing Clear Security Objectives:
Define clear objectives that are aligned with your organisation's business goals for S/4. Your role design comes into this again and so does your strategy for deciding on how you deliver access into the new system using Fiori
Develop a security roadmap outlining the specific tasks, milestones, and timelines for achieving your security objectives throughout the S/4 HANA migration project.
3. Engaging Stakeholders Across Departments:
Our “it’s good to talk” mantra is all about taking every opportunity to engage all stakeholders in SAP security.
Foster collaboration and communication among stakeholders from various departments, including IT, security, compliance, finance, and operations, to gain a holistic understanding of security needs and priorities.
Encourage active participation and buy-in from executive leadership to ensure that security considerations are integrated into strategic decision-making processes and resource allocation discussions.
4. Segregation of duties and financial risk:
If your SoD’s are well managed, ensure your strategy will play forward into the new world of S/4. If not, now is the perfect time to be planning to get this critical area under control.
Prioritise risks based on their likelihood and potential impact on business operations, regulatory compliance, and reputation, ensuring that mitigation efforts are focused on addressing the most critical threats first.
Establish risk acceptance criteria and mitigation strategies in collaboration with key stakeholders to ensure alignment with risk tolerance levels and strategic objectives.
By following these steps during the early planning stage, you can lay a solid foundation for implementing robust security measures that are aligned with business goals and risk management priorities. Early identification of security risks and key project needs can help mitigate potential disruptions, safeguard sensitive data, and ensure the success of the S/4 HANA migration implementation.
Aligning Business Solutions with Security Measures
Integrate security considerations into every stage of your S/4 HANA migration, from planning and design to implementation and ongoing maintenance. Again, make sure your security team is taking every opportunity to bring all the various stakeholders along with them, taking every opportunity to get everyone engaged in security and bought into what the team is doing and why.
A word of caution on complexity: It’s easy to design in complexity without even trying. Now is the time to be thinking about optimising everything. Ensure that security controls are aligned with business processes to mitigate risks without hindering operational efficiency.
Cost-Effective Security Solutions
The biggest consideration for the security element of your project in relation to cost effectiveness is whether or not to adopt a new role design. The Pumpkin view is that an S/4 project is the perfect time to address your role design if the current one is not fit for purpose. Not taking the opportunity to sync your latest requirements to your role design will likely cost you more down the line.
By proactively addressing SAP security considerations as you begin and then throughout your S/4 HANA migration or implementation journey, you can minimise risk, optimise resource utilisation and ensure the long-term success of your project.
Remember, security is not just a technical requirement but a fundamental aspect of business resilience and competitiveness. If you have any questions or need further guidance on SAP security best practices, get in touch, we're here to help.